Reverse engineering of compiler-generated, unmanaged code (such as C++, C, assembler, …) is usually a difficult and time-consuming process. This is because the code is compiled directly into native machine code. Managed code like C# or Java is different. Their advantage of being able to run device-independently is their disadvantage in the case of security. The programming language of Unity is C#. C# is compiled to Intermediate Language (IL), not machine code that could run directly on your computer. The IL is stored in a file called assembly (*.dll), along with metadata describing its classes, methods, and attributes. On different machines this IL will be interpreted differently. Attackers can easily parse this IL and convert it into source code.
Let’s have a look at this simple example source code:

Building this example as assembly with .Net Compiler will result in IL looking like this:
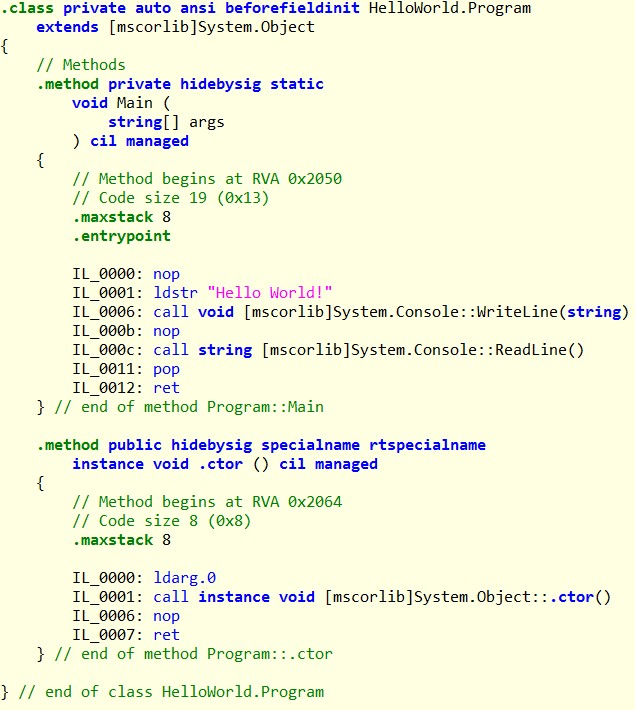
Interpreted by decompilers used for reverse engineering, it will look like the original source code:
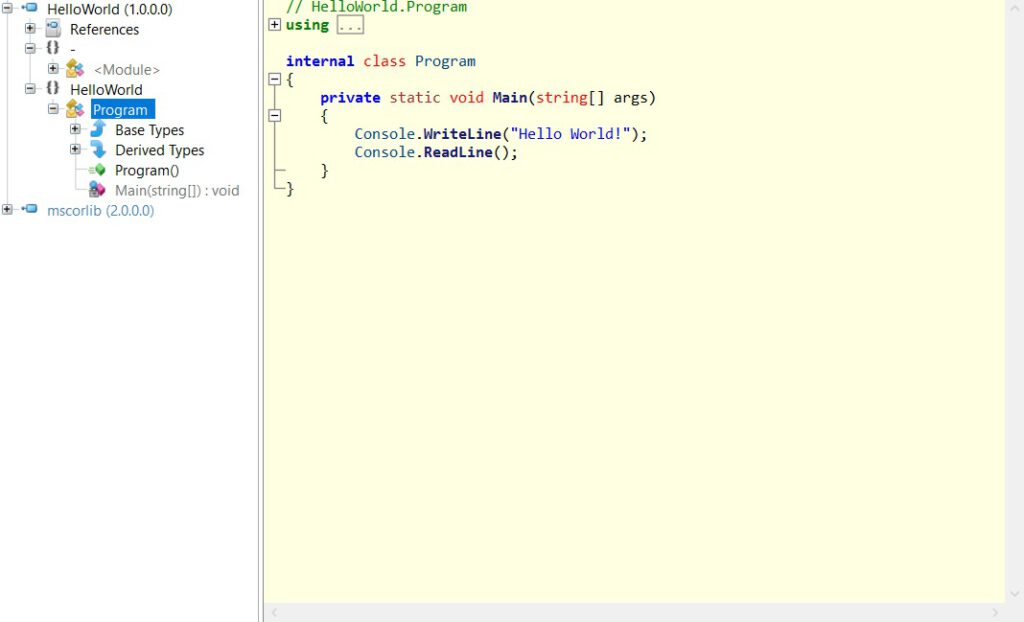
To secure against this decomplication you can use techniques to harden the source code, deliberately constructed to resist analysis. We refer to such techniques for hardening programs under the general umbrella “Obfuscation”.
Some examples of situations where obfuscation can be applied are as follows:
■ Intellectual property protection – Many commercial programs have some form of protection against unauthorized duplication. Some systems use further obfuscation to hide the implementation details of certain parts of the system. Good examples include Skype, Apple’s IMessage, and even the Dropbox client, which use obfuscation to protect their communication protocol formats.
■ Digital rights management – DRM schemes typically protect certain important information (e.g., cryptographic keys and protocols) through obfuscation. Apple’s FairPlay, Microsoft’s Media Foundation Platform, and its PlayReader DRM, to name just two, are examples of the use of obfuscation. Currently, this is the leading contemporary application of obfuscation.
Abstractly speaking, “obfuscation” can be viewed in terms of program transformations. The goal of such methods is to take as input a program and produce as output a new program that has the same computational effect as the original program (formally speaking, this property is called semantic equivalence or computational equivalence), but at the same time is “harder” to analyze.
An obfuscation of the above could look like the following:
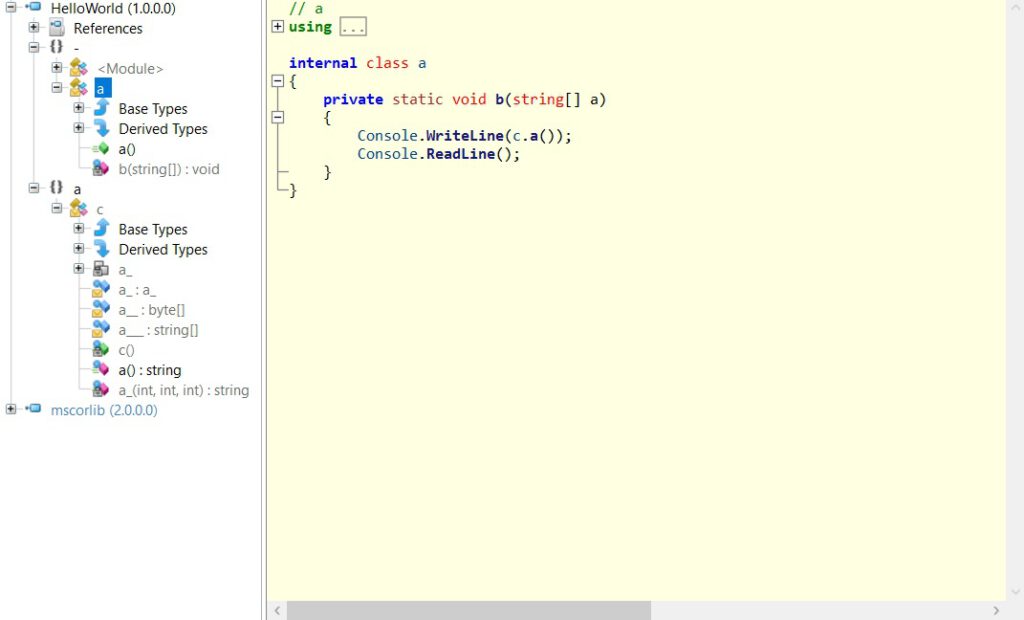
A software offering this kind of obfuscation, is GuardingPearSoftwares Obfuscator. Using multiple techniques, it secures against code analyzation and/or manipulation.
The includes techniques with description, can be looked up here: “Obfuscator Setting“.
Additionally, GuardingPearSoftwares Obfuscator offers a unique feature. It comes with a StackTrace Deobfuscator. Following exceptions in a obfuscated and build assembly is on purpose hard, but with the handy GuardingPearSoftwares StackTrace Deobfuscator follow up. Have a look how to use and activate it here: “StackTrace deobfuscation“.
