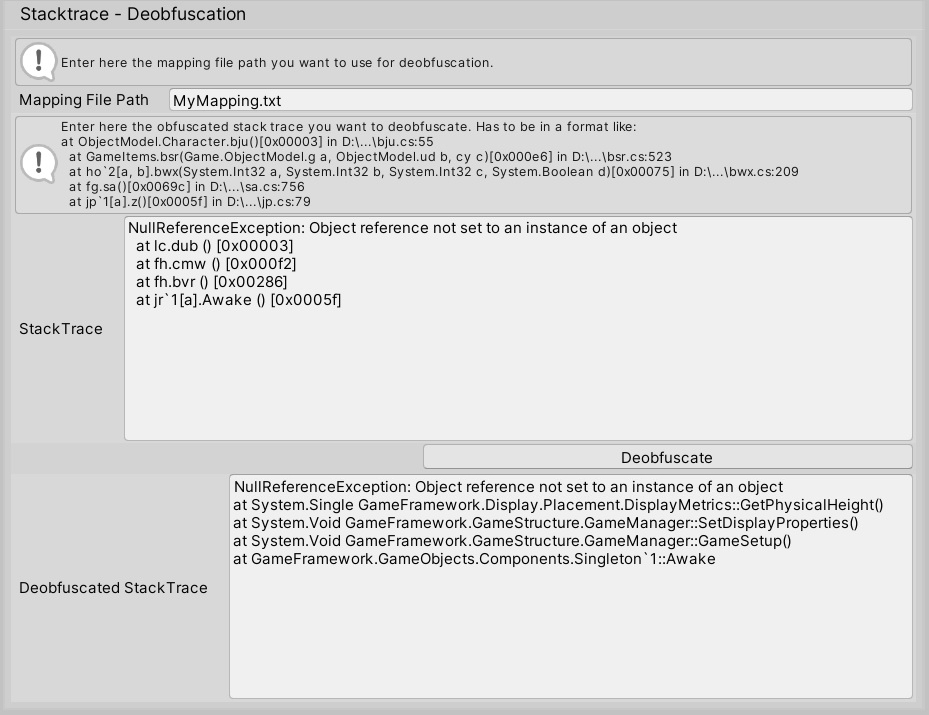
One of the side effects of obfuscation is the difficulty of debugging obfuscated code. User-generated and reported exceptions typically contain obfuscated methods and class names, making it nearly impossible to trace the stack trace in the source code. GuardingPearSoftware’s obfuscator makes it possible to generate a detailed mapping containing the obfuscated entities and their original names. This information is essential for the developer when interpreting the debugger output of the obfuscated assembly.
Enable the mapping generation in the settings. You can find it at OPS->Obfuscator->Setting under the “Optional” Tab in the “Renaming Component”.
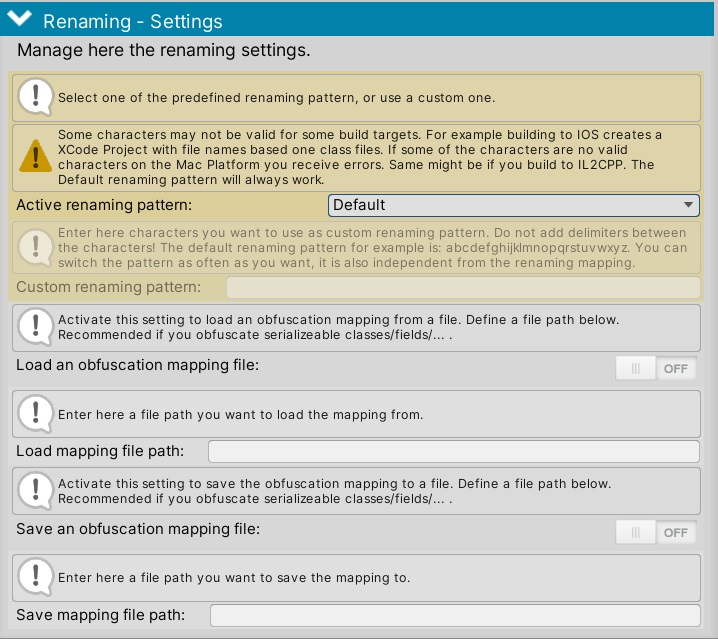
Additionally, you must specify a path to save the mapping. (The relative path is your Unity project directory).
Now, when you build your game with Obfuscator enabled and enter a file path/name, a Json-based mapping file is created in the location you selected.
To load this mapping and use it for deobfuscation, you need to go to the Error Stack Trace Deobfuscator at OPS->Obfuscator->Error Stack Trace.
Enter your mapping file path and the code you want to deobfuscate. Press the “Deobfuscate” Button.